Stealth Crypto Heist: New Malware Hijacks Computers to Mine Monero (XMR) in the Shadows
Cybercriminals are upping their game—and your CPU might be their latest pawn. A newly discovered malware strain is quietly turning infected machines into Monero-mining zombies, siphoning crypto while victims remain none the wiser.
How it works: The malware slips past defenses, installs a hidden mining script, and starts cranking out XMR. No flashy ransomware demands, no data leaks—just your processor grinding away for someone else’s profit.
Why Monero? Privacy features make XMR the go-to for shady ops. Unlike Bitcoin, transactions stay off the radar—perfect for hackers who’d rather not explain their sudden Lambo purchase to the IRS.
Defense tip: Update your OS, ditch sketchy downloads, and monitor CPU usage. If your fan’s screaming during a Zoom call, you might be funding a hacker’s yacht—or at least their crypto trading addiction.
Final thought: Wall Street still thinks crypto is a scam? Meanwhile, hackers are running a shadowy, decentralized hedge fund—with your laptop as their unwilling investor.
A Silent Virus Could Be Using Your Computer For Crypto Mining
According to cybersecurity firm Fortinet, attackers gain access by exploiting known software vulnerabilities. These include Log4Shell and Apache ActiveMQ, which many systems still use.
Once inside, the virus installs a tool called XMRig, a legitimate open-source miner.
But instead of asking for permission, it runs in the background, using your computer’s processing power to earn Monero for the hackers.
Also, H2Miner uses smart scripts to disable antivirus tools. It alsothat may already be running on the system.
Then, it wipes any trace of its actions. On Linux, it installs a cron job that redownloads the malware every 10 minutes.
On Windows, it sets up a task that runs silently every 15 minutes.
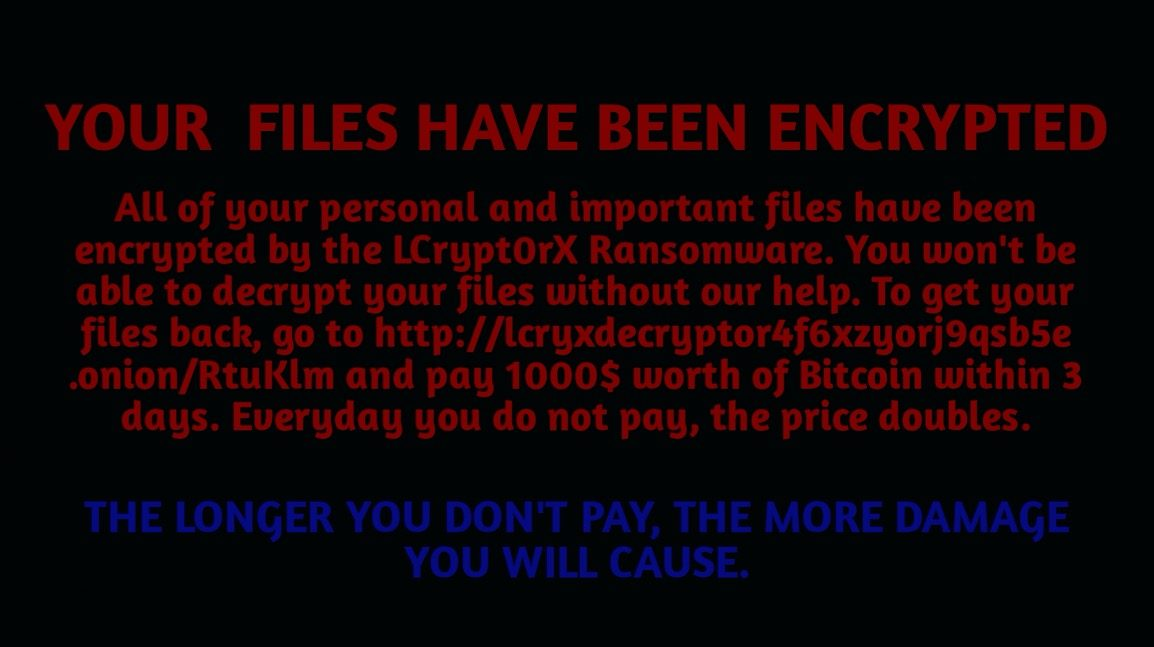
A Ransomware Twist Adds More Damage
The virus doesn’t stop at crypto mining. A new payload, called Lcrypt0rx, can also.
It uses a simple but destructive method to overwrite the—a key part of your computer that controls startup. This can prevent the system from booting properly.
The ransomware also adds fake system settings to hide itself and create persistence.
The campaign takes advantage ofand misconfigured services. Once a machine is infected, the malware scans for other systems to infect—especially Docker containers and cloud platforms like Alibaba Cloud.
It also spreads through USB drives and loops through antivirus processes, killing them off one by one.
Security experts warn that removing H2Miner requires a. You must delete all related cron jobs, scheduled tasks, and registry entries.
If even one hidden script survives, the botnet can reinstall itself and resume mining Monero in secret.
What Traders and Crypto Users Should Know
This attack isn’t targeting crypto wallets directly. Instead, itto generate new Monero coins for the attackers.
The risk is especially high for.
If your system runs hot or slows down unexpectedly, you might want to check for unusual processes likeor recurring outbound connections.
Monero’s privacy features make it attractive for attackers. But for users, the real risk is losing control of your devices—and unknowingly funding crypto crime.

