Hackers Pivot from Mixers to Bridges in High-Speed Crypto Laundering Scheme, Experts Reveal
Cybercriminals are ditching old-school mixers for blockchain bridges—turbocharging their money-laundering ops. Here’s how they’re staying ahead of the game.
Subheading: The New Laundry Route
Forget slow-and-steady mixers. Bridges let hackers move dirty crypto across chains in seconds—no paper trail, no waiting. Analysts call it the 'DeFi dark alley' for a reason.
Subheading: Regulators Left in the Dust
While compliance teams scramble to track cross-chain hops, hackers laugh all the way to the (unregulated) bank. Another win for crypto’s wild west era—and another headache for the suits.
Closer: Next stop? Probably a yacht paid for with your stolen NFTs. But hey—at least the blockchain’s transparent, right?
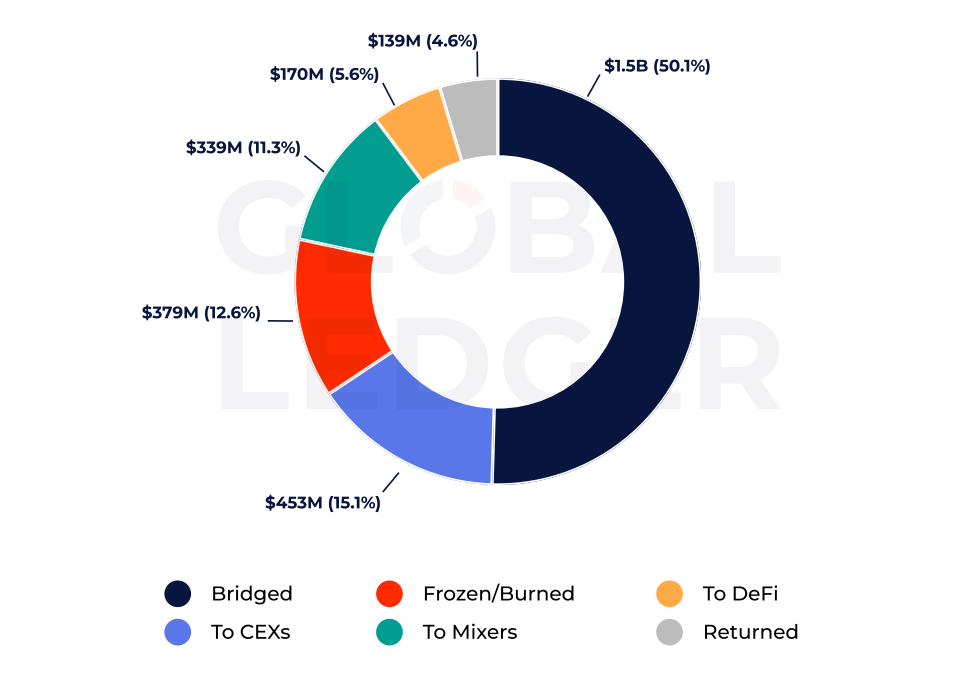 Hackers laundered 4.4x more via bridges than mixers in H1’25 | Source: Global Ledger
Hackers laundered 4.4x more via bridges than mixers in H1’25 | Source: Global Ledger
“Attackers are moving faster, often laundering funds before the incident is even publicly known,” the report states. In one case, the fastest movement of hacked funds took just four seconds, effectively giving attackers a head start measured in blinks of an eye. This rapidity severely limits the ability of current alerting systems and regulators to intervene before the money disappears.
By breaking down timelines, the analysts identified key patterns in how stolen assets are handled: how quickly they move, how long they remain idle, and which parts of the crypto ecosystem are most exploited.
“Knowing these timing patterns can help detect suspicious activity sooner and reduce the window attackers have to launder funds. It is not just about reacting, it is about anticipating the next move.”
Global Ledger
Bridges outpace mixers as laundering tools
Perhaps the most significant finding concerns the methods hackers use to obscure the origin of stolen crypto. Cross-chain protocols — also known as cross-chain bridges — have apparently become the preferred method for laundering stolen crypto.
In the first half of 2025, over $1.5 billion, or 50.1% of all hacked assets, were routed through bridges. This dwarfs the $339 million — around 11% — sent to crypto mixers, which nonetheless remain in use in about half of hack cases.
As Global Ledger notes, the functionality of cross-chain protocols is “heavily Leveraged by illicit actors, making them a key tool for obfuscating stolen funds origin.” The report suggests that bridges are overtaking mixers as the preferred laundering tool “likely due to their speed, liquidity, and lower regulatory scrutiny.”
Mixers like Tornado Cash, which scramble funds by mixing them with others to break traceability, were once the standard for laundering crypto stolen in hacks. Bridges, which allow assets to be transferred quickly between different blockchain networks, now seem to provide more rapid movement and access to multiple liquidity pools, making it easier for hackers to move large sums swiftly and complicate tracing efforts by law enforcement.
Crypto exchanges remain the main cash-out points
Another area of insight concerns where stolen funds ultimately land. Approximately 15% of hacked assets — $453 million — flowed into centralized exchanges, which are “highly likely to be used for further cash-out,” the analysts say. In contrast, decentralized finance platforms received only about a third of that amount, roughly $170 million or 5.6%.
Despite the rapid growth of DeFi usage and total value locked, the report underscores that centralized platforms remain the primary off-ramp for laundering stolen funds, suggesting that, for all their promise, DeFi protocols have yet to supplant traditional exchanges as the go-to destinations for hackers seeking to convert crypto to fiat or less traceable assets.
The report also paints a sobering picture regarding recovery efforts. Of the total stolen amount, nearly 13% — $379 million — was frozen or burnt, likely due to coordinated enforcement actions or security measures. Meanwhile, only a small portion, 4.6% — around $140 million — was voluntarily returned.
As Global Ledger says, enforcement efforts are making some impact, “but voluntary returns remain rare,” emphasizing that “most recovery still depends on rapid intervention, not goodwill.”
Only a matter of time
A critical takeaway is the alarming speed with which attackers act. Funds from nearly one in four hacks were fully laundered before any public disclosure occurred, closing the window for law enforcement to track or freeze assets. The fastest complete laundering process — from theft to last deposit — was a mere two minutes and 57 seconds, barely enough time to blink.
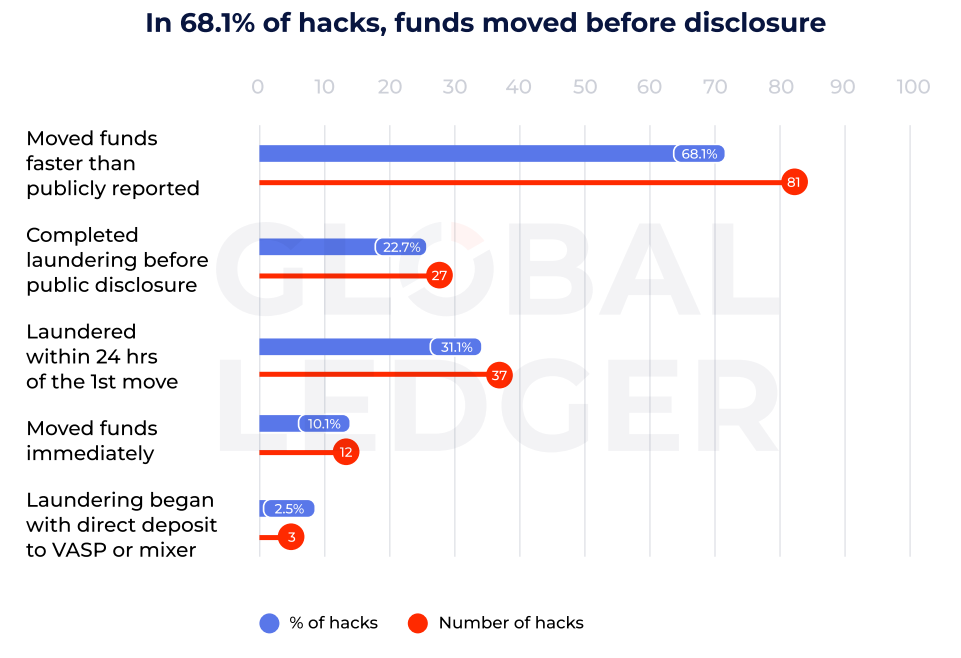
“Speed has become the new dangerous weapon,” the report warns, noting that the quickest movement of stolen funds was “over 75 times faster than the alerting system.” Once funds begin moving, the trail can go cold in hours or even minutes. Attackers clearly exploit this narrow response window: in over 30% of cases, illicit actors completed laundering within a day of the first wallet movement.
At the time of the report’s research, $1.6 billion — or 53.6% of total losses — remained unspent, meaning these funds either did not move or their movement stopped. The report suggests that some of this amount is “likely still in the process of being laundered, as attackers may be waiting for the heat to die down.”

