Crypto Under Siege: Human Errors and AI-Driven Hacks Wreak Havoc in 2025
Crypto's Achilles' heel strikes again—human fallibility meets machine precision in a brutal 2025 security storm.
When flesh and code fail together
Self-custody nightmares unfold as wallet-draining combo attacks exploit both tired traders and overconfident smart contracts. The 'unhackable' narratives of 2024 now read like tragicomic fiction.
AI adapts faster than compliance departments
Next-gen phishing bots now mimic CEX support teams with terrifying accuracy, while liquidity pool exploits execute in the time it takes a VC to tweet 'fundamentals are strong.'
The bitter irony? These breaches are funding crypto's most sophisticated white-hat teams—talk about regenerative finance. Maybe banks had a point about those 'pesky security standards' after all.
Access control
According to a Hacken research report shared with crypto.news, access control failures remain the biggest problem, accounting for roughly 59% of losses, or about $1.83 billion in the first six months alone.
The largest case was the infamous theft of $1.46 billion from Bybit, where North Korean attackers exploited a compromised Safe{Wallet} signer interface to push a malicious transaction. As Hacken explained the malicious proposal “manipulated the Safe’s delegate call setup to seize control of the wallet.” As of late July, Bybit’s bounty portal tracking the funds shows that over 80% of the stolen assets have vanished without a trace.
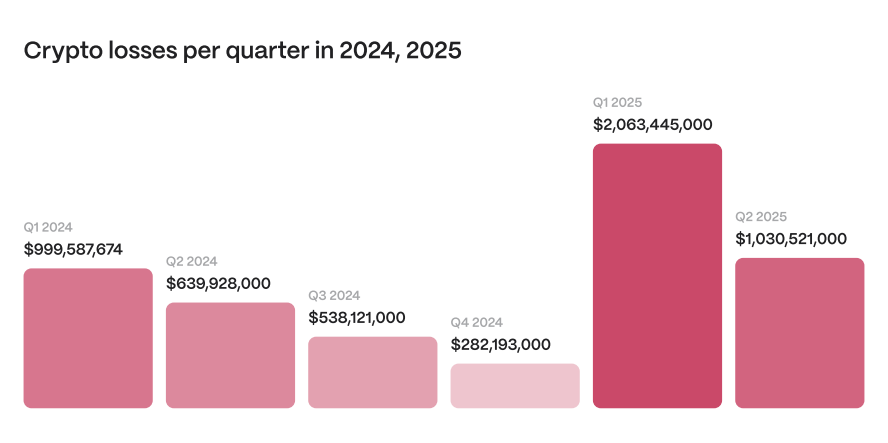
Other big, eyebrow-raising hacks included UPCX losing about $70 million after attackers hijacked an admin account, KiloEx suffering a $7.5 million exploit through oracle price manipulation, and an insider secretly backdooring the Roar staking contract to drain $800,000.
As if that wasn’t enough, multi-sig wallets weren’t safe either as one on zksync was basically a single-signer wallet, letting attackers steal around $5 million. Politically motivated attacks also happened, like Iran’s Nobitex losing over $90 million in crypto.
Phishing and engineering
Phishing and social engineering scams made up close to $600 million (about 19%) of losses, per Hacken. One big incident involved an elderly U.S. victim who was tricked into transferring $330 million in Bitcoin (BTC). Hacken notes this was “one of the largest reported individual thefts,” adding that the theft “reflects the emotional and trust-based manipulation used by attackers beyond pure technical exploits.”
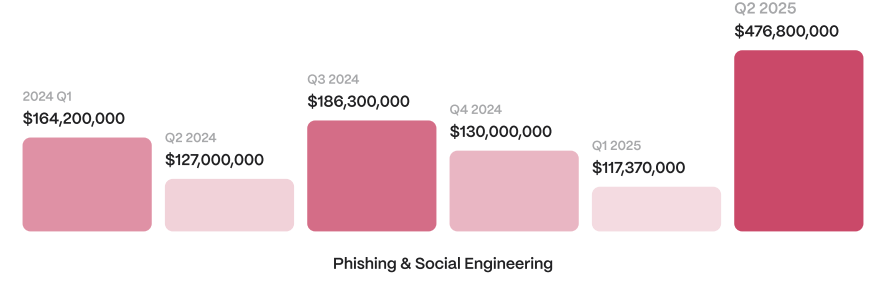
Another neverending problem: scammers keep targeting wealthy Coinbase users by impersonating support staff, reportedly stealing over $100 million after a data breach exposed contact info.
“Callers posing as ‘Coinbase support’ quoted real balances to gain trust and trick victims into revealing keys or passcodes, stealing over $100 million to then launder stolen money via mixers, OTC desks and DeFi.”
Hacken
Smart contract bugs caused about $264 million in losses, roughly 8.8% of the total. The most biggest was the Cetus hack, where an overflow bug let attackers drain $223 million in just 15 minutes, marking the worst DeFi quarter since early 2023. Hacken notes that if there had been real-time TVL monitoring with auto-pause, up to “90% of those funds could have been saved.”
Bots are everywhere
Artificial intelligence-related exploits are also quickly becoming a serious threat, with Hacken reporting a 1,025% surge in such incidents compared to last year, nearly all linked to insecure APIs. The report flags major vulnerabilities like remote code execution flaws in Langflow and BentoML, along with prompt injection attacks targeting commercial LLMs, underscoring how fast this attack vector is evolving.
As Hacken puts it, the promise of AI “is massive, but so are the risks,” highlighting the urgent need for “AI-specific security protocols alongside traditional blockchain safeguards.”
The report also points to a broader issue: many web3 projects still struggle with operational maturity. Hacken emphasizes that the “fragmented state of wallet and key access governance across the Web3 space” results from factors like lack of formal access control frameworks tailored for blockchain, poor off-chain process security, and weak UX protections against social engineering.
Off-chain still matters
To help close these security gaps, analysts at Hacken suggest combining the cryptocurrency Security Standard for managing on-chain keys with ISO/IEC 27001 for strengthening off-chain processes and meeting compliance requirements. Hacken’s compliance lead says using both frameworks — along with proper team training — can lower risks while building trust, enabling growth, and keeping customers confident over the long term.
Simply put, the first half of 2025 confirms that crypto security is still a fast-moving target, just as unpredictable and challenging as ever. Most losses continue to come from access control issues, phishing attacks are picking up speed, smart contract flaws remain costly, and AI-related risks are quickly gaining ground.
Hacken’s findings suggest that staying SAFE in this space will take more than just code audits as it’ll require a layered defense strategy combining technical tools, solid internal practices, user awareness, and protections tailored to AI threats to stay ahead of increasingly skilled attackers.

