Zombie Crypto Mixer eXch Still Laundering Funds—Closure Was Just Theater
Another day, another ’shuttered’ dark finance tool doing brisk business. The notorious crypto mixer eXch—supposedly shut down in 2023—keeps processing dirty transactions while regulators play whack-a-mole.
Forensic blockchain analysts report fresh inflows from ransomware gangs and sanctioned entities. The mixer’s operators now use decentralized bridges and privacy coins to bypass detection—because nothing says ’financial innovation’ like helping North Korea evade sanctions.
Meanwhile, three-letter agencies keep issuing stern press releases. Because clearly, that’s worked so well against $100B+ in annual crypto crime.
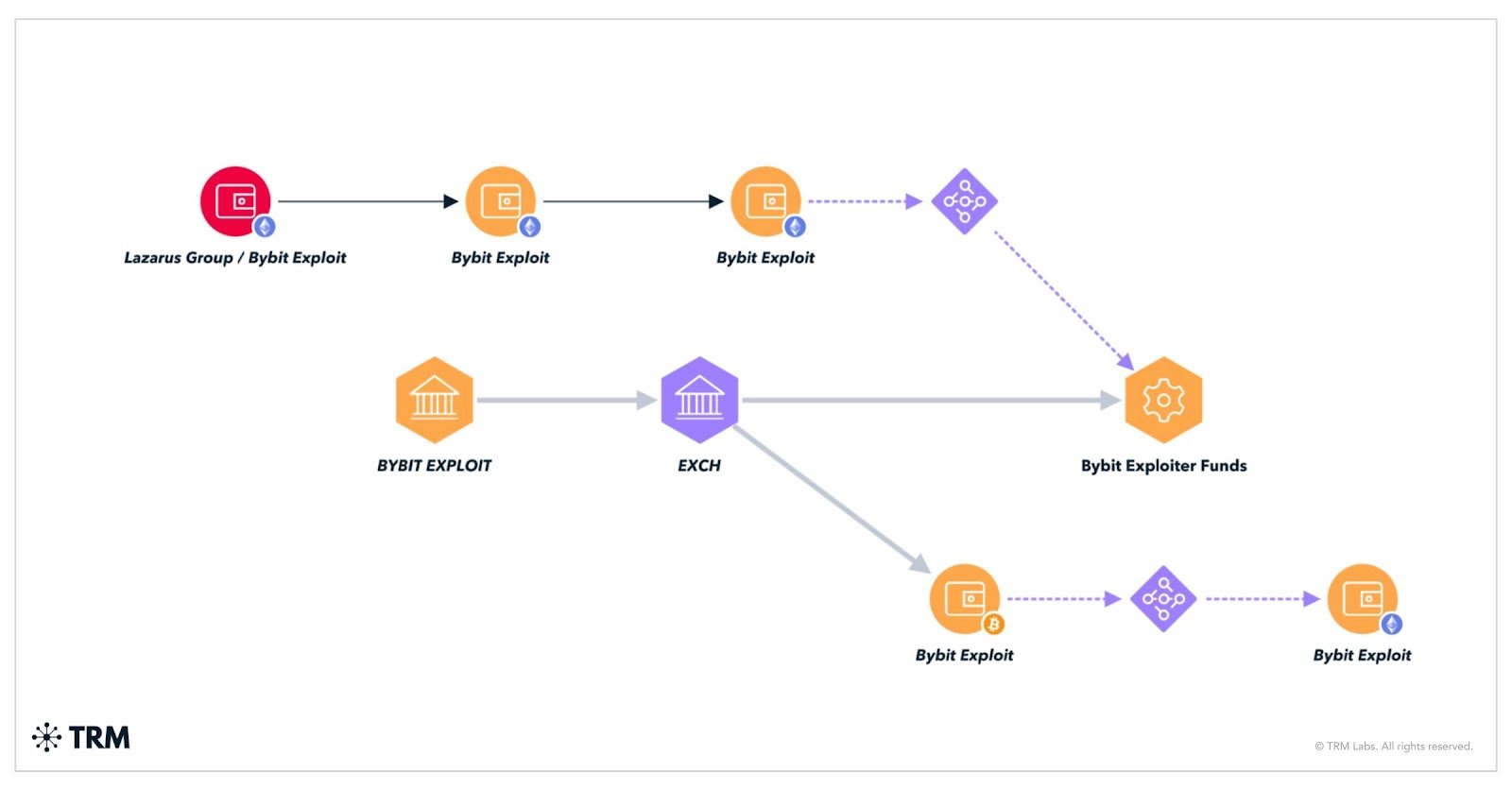 Example Flow of Bybit exploit funds moving through eXch and bridging back and forth between ETH and BTC | Source: TRM Labs
Example Flow of Bybit exploit funds moving through eXch and bridging back and forth between ETH and BTC | Source: TRM Labs
The analysts have linked eXch to significant criminal activity, including a long-term association with child abuse material threat actors.
“We have identified that eXch has been directly exposed to more than $300,000 in CSAM-related funds. However, we expect this figure to increase as we continue our attribution on eXch.”
TRM Labs
The exchange’s mixed-pool mechanism, designed to fragment transactions, has raised red flags for investigators. TRM Labs explained that in a mixed pool “all received and sent transactions are mixed together and there is no way to discover how many people are behind certain addresses and traceability is extremely difficult.” This lack of transparency complicates risk assessments, as illicit deposits may be linked to legitimate withdrawals, the analysts added.
Crypto mixer eXch announced its official shutdown on April 17. However, the protocol removed the message a few hours later — leaving “no public record of its communication on this topic,” and on April 28, the platform resumed operations, TRM Labs says.
As eXch’s team earlier said, the project had become the target of a “transatlantic operation” aiming to shut it down and potentially prosecute key figures for money laundering and terrorism. Blockchain analytics firms like Elliptic and others flagged eXch as a key hub in the laundering process.
Following the Feb. 21 theft that drained over 400,000 Ethereum (ETH) from Bybit’s cold wallet, the Lazarus Group used a web of decentralized exchanges, cross-chain bridges, and privacy tools, including eXch, to hide the stolen assets’ origin.

