North Korea’s Cyber Warfare Unit Unveils Advanced Crypto-Targeting Tactics
Pyongyang’s shadowy hacking collective Lazarus Group has leveled up—again. Their latest toolkit bypasses conventional exchange security measures, drains wallets with surgical precision, and leaves fewer fingerprints than ever before.
How They’re Doing It:
Spear-phishing campaigns now mimic institutional crypto services, while smart contract exploits target DeFi protocols hungry for TVL. Meanwhile, Western regulators still debate whether NFTs are securities.
The Irony:
These attacks fund ballistic missile tests—effectively making crypto traders unwilling sponsors of Kim Jong-un’s military parades. Talk about involuntary yield farming.
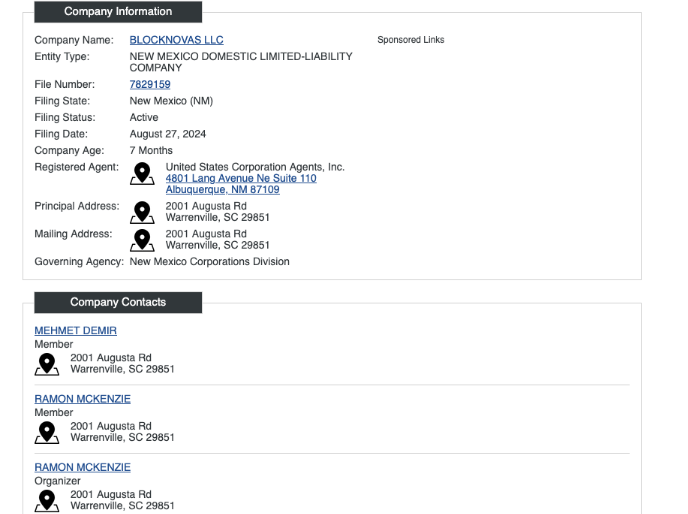 Source: Silent Push
Source: Silent Push
The researchers have discovered another business,, which has connections to this scheme. However, this one doesn’t seem to be registered in the US. Of the three, Blocknovas is the most active front company, the report says.
Notably, Kasey Best, director of threat intelligence at Silent Push, was quoted by Reuters as saying that, “this is a rare example of North Korean hackers actually managing to set up legal corporate entities in the US in order to create corporate fronts used to attack unsuspecting job applicants.”
Furthermore, this attack is similar – and may be linked – to the attempted data theft recently reported by a number of crypto industry insiders.
Nick Bax of the, shared last month that a threat group is working to steal data and funds through fake business calls on.
Having audio issues on your Zoom call? That’s not a VC, it’s North Korean hackers.
Fortunately, this founder realized what was going on.
The call starts with a few "VCs" on the call. They send messages in the chat saying they can’t hear your audio, or suggesting there’s an… pic.twitter.com/ZnW8Mtof4F
The attackers’ goal is ‘simple.’ Attract crypto developers and infect their devices with malicious software via a LINK they send during the interview. They may be pretending to experience technical issues, for example, and will ask the target to click on a link.
Bax said the threat group stole “$10s of millions of dollars” using this tactic, and others continue to copy it.
You might also like Lazarus Group Deposits 400 ETH to Tornado Cash, Hackers Target Crypto Vets on ZoomContagious Interviews and Malicious JavaScript
Silent Push says that what it found is a new campaign. The entity behind it is the North Korean APT (advanced persistent threat) group’ This is a subgroup of the notorious state-sponsored.
Best told Reuters that the job interviews “lead to sophisticated malware deployments in order to compromise the cryptocurrency wallets of developers.” Also, they target the developers’ passwords and credentials, possibly to use them in “further attacks on legitimate businesses.”
Per the report, Silent Push confirmed “multiple victims” of the latest interview campaign.
However, thehas seized Blocknovas’ domain “as part of a law enforcement action against North Korean Cyber Actors who utilized this domain to deceive individuals with fake job postings and distribute malware.”
The other two websites are still operational at the time of writing.
But this is not all. Another highly sophisticated line of attack is inserting malicious JavaScript intorepositories and NPM packages.
Lazarus began this campaign in August 2024, stealing funds and data through supply chain attacks. Furthermore, this attack vector is evolving.
Notably, the malware, called Marstech1, targets popular crypto wallets. Various reports have named,, and.
Cybersecurity companyfound 233 victims who installed the Marstech1 implant between September 2024 and January 2025.
You might also like New Malicious Campaign Targets Atomic and Exodus Wallets
