Crypto 2025: $3.4 Billion Vanishes in Cybersecurity’s Darkest Year Yet
Digital vaults bled billions this year—and the industry's shiny promises couldn't stop the hemorrhage.
The Breach Breakdown
Attackers didn't just pick locks; they rewrote the rules. Cross-chain bridges became digital highways for heists, while 'audited' smart contracts folded like cheap suits. Remember when 'code is law' was the mantra? Thieves treated it like a suggestion.
Where the Money Went
That $3.4 billion didn't evaporate—it got rerouted. Some vanished into mixer tornadoes, other chunks landed in wallets tagged by the FSA. A cynical slice probably funded someone's 'legit' DeFi yield farm—the ultimate wash trade.
The Security Shell Game
Firms scrambled, rolling out patches that were Band-Aids on bullet wounds. Insurance pools? Drained. Bug bounties? A rounding error compared to the losses. The 'trustless' ecosystem learned a painful truth: you're only as secure as your weakest link—and 2025 had chains made of paper.
The Aftermath & The Grift
CEOs tweeted 'funds are safu' until they weren't. Regulators sharpened their pencils—and their claws. Meanwhile, the same VCs that hyped 'unhackable' protocols quietly pivoted to selling cybersecurity SaaS. Funny how the cure always profits from the disease.
So here we stand at year's end: a industry built on transparency, staring at a $3.4 billion black hole. The tech promises a revolution, but the balance sheet screams cautionary tale. Maybe next year's innovation won't be a new blockchain—but a vault that actually closes.
 Read us on Google News
Read us on Google News
In Brief
- Three giant hacks accounted for 69% of recorded crypto losses in 2025.
- North Korea stole more than $2 billion in cryptocurrencies through infiltration and cunning.
- Personal wallets were massively hacked despite lower stolen amounts per user.
- DeFi protocols show unexpected stability thanks to new proactive security tools.
Hackers on the attack: the era of “Big Game Hunting”
They no longer look for the small badly protected wallet. Hackers in 2025 want heavy, massive targets. They hunt the “whales,” those centralized platforms that hold funds from thousands of users. And the result is frightening: $3.4 billion stolen this year. The hacking of the Bybit exchange alone represents 1.4 billion in losses.
According to Chainalysis, only three attacks account for 69% of total losses in 2025. An unprecedented concentration. And a strong signal: hackers now rely on surgical but devastating operations.
Private keys are still in the crosshairs. But it is especially internal vulnerabilities, human errors, and poorly managed authorizations that open the door to attacks. These large platforms, despite being heavily secured, become the target of a “big game hunting” orchestrated by actors who take the time to observe, infiltrate, and strike.
As Andrew Fierman, national security director at Chainalysis, says:
It is difficult to predict if 2026 will be worse, as hacks often depend on a few isolated events — one or two massive hacks can be enough to break annual records. But what I can say is that the “big game hunting” trend continues, and there is no indication that hacks will decrease next year.
Crypto plundered: Pyongyang pulls off the heist of the century
Among the most formidable actors of the year, one name keeps coming up: North Korea. The Pyongyang regime has stolen more than $2.02 billion in crypto-assets. An absolute record, up 51% compared to 2024. But it is not just a matter of numbers. It is a matter of strategy.
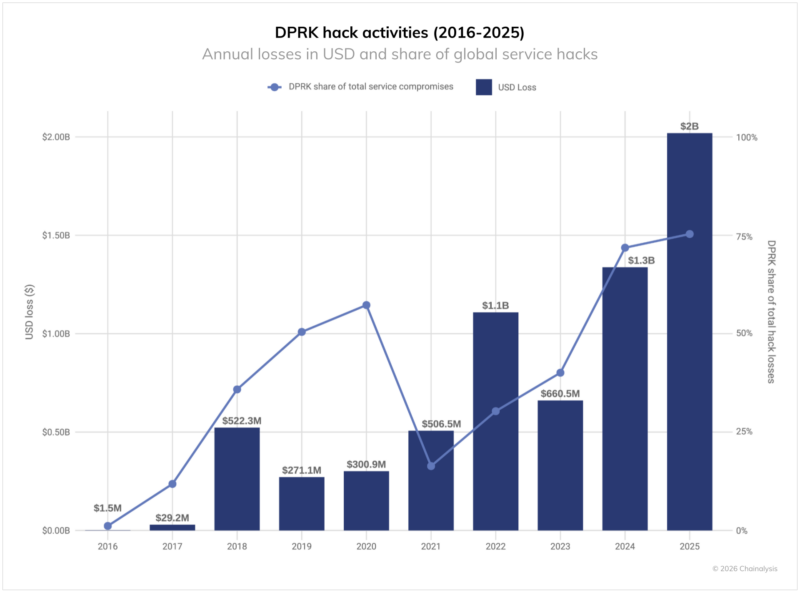
North Korean hackers no longer are content with simple intrusions. They infiltrate by posing as developers, recruiters, or investors. Once inside, they target critical access, copy source codes, bypass VPNs, and inject their poison through fake interviews or fake fundraising.
The theft does not stop there. It is followed by a sophisticated laundering process spread over 45 days. DeFi, mixing services, cross-chain bridges, Chinese platforms… Everything is used. With almost military precision.
The regime constantly trains and perfects new tactics enabling its agents to execute their operations, whether by infiltrating Web3 companies as developers or exploiting vulnerabilities through third-party providers.
Andrew FiermanThis is no longer just hacking. It’s a shadow war, with crypto as the battlefield and data as weapons.
Personal crypto wallets: the invisible threat that explodes
While the spotlight is on the big attacks, another reality is playing out in the shadows. That of the 158,000 hacks of personal wallets recorded in 2025. A threefold increase since 2022. And 80,000 unique victims identified.
The paradox? Less money stolen per user. In 2024 individual losses represented 1.5 billion. This year, “only” 713 million. Hackers adapt: more victims, smaller amounts, but still a significant overall loot.
The ethereum and Tron blockchains are the most affected, despite their robust architectures. It may be the massive use of these networks that makes them more vulnerable. More wallets, more applications, more opportunities for hackers.
Conversely, DeFi surprises with its resilience. Its locked value has more than doubled since 2023, reaching $119 billion, without triggering a new wave of hacks. A striking contrast. This is partly explained by the rise of proactive monitoring solutions like Hexagate, which enable reaction within hours.
5 numbers that summarize a digital nightmare
- $3.4 billion stolen in the crypto ecosystem in 2025;
- $1.4 billion siphoned in a single attack (Bybit);
- $2.02 billion stolen by North Korea;
- 158,000 individual wallets compromised;
- $119 billion locked in DeFi without a spike in hacks.
Crypto hacks will not disappear overnight. They adapt, change form, and target where attention is weakest. But faced with these threats, solutions exist. Cold wallets, enhanced authentication, diversification of security tools… The best defense remains constant vigilance. Because in this ever-evolving universe, prevention is better than cure.
Maximize your Cointribune experience with our "Read to Earn" program! For every article you read, earn points and access exclusive rewards. Sign up now and start earning benefits.

