Address Poisoning Scam: How a $50M Crypto Heist Unfolded
A new breed of digital theft just siphoned $50 million from crypto wallets—and it didn't need a single password.
How the Attack Works
Forget brute force. This scam relies on human error and transaction history sleight-of-hand. Attackers send tiny, seemingly harmless transactions from a wallet address that looks almost identical to one in your history. The goal? Poison your transaction log with a fake address you might copy and paste later.
When you go to send funds to a legitimate contact, you scroll through your history, pick what looks like their address, and unknowingly send your crypto straight to a scammer's wallet. No smart contract exploits, no private key leaks—just a simple, devastating misdirection.
The $50M Wake-Up Call
The sheer scale of this loss exposes a critical vulnerability: our over-reliance on auto-filled data and visual verification. It's a stark reminder that in decentralized finance, your transaction history can be weaponized against you. The industry preaches 'self-custody,' but moments like this make it feel more like self-sabotage.
Staying safe means manually verifying every character of a destination address for every single transaction. No shortcuts. Because in crypto, the most expensive mistake you can make is trusting your own records.
What Happened? The Tragic $50 Test Transfer
A crypto user sent a small $50 USDT test transfer to their own wallet address, which triggered an address poisoning attack and caused a $50 million loss.
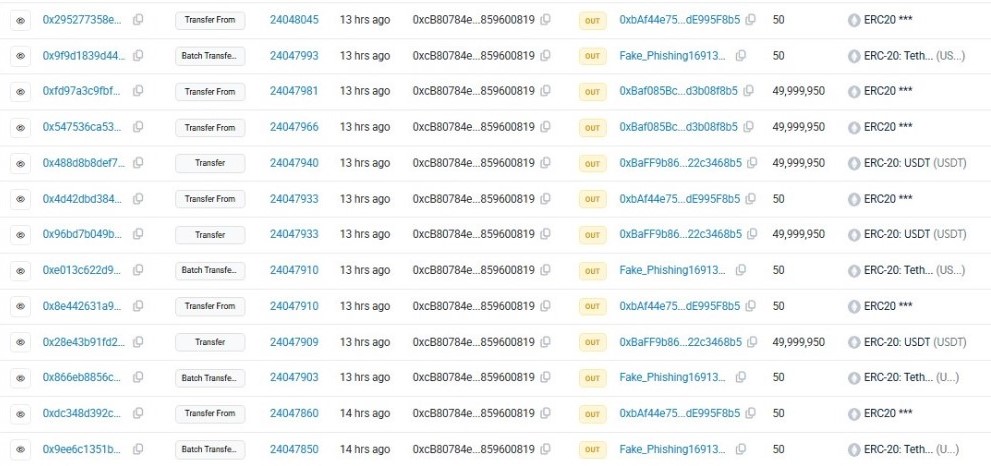
Address poisoning is a type of scam that doesn't involve hacking into systems or stealing private keys. Instead, it preys on human habits and convenience.
How the Attack Actually Worked?
After the victim sent the small test transfer, the scammer quickly took advantage of the situation. They deployed a fake wallet address, almost identical to the victim’s, with the same first and last characters. This exploit took advantage of the fact that most wallets hide the middle of an characters with “...,” making it hard to distinguish real and fake addresses.
When the victim later went to send $50 million USDT, they simply copied the address from their previous transaction history, trusting the familiar starting and ending characters. Unfortunately, they didn’t check the middle character, and the scammer had already replaced it. The funds were transferred in one click, and the $50 million was gone.
In the aftermath, the stolen USDT was quickly swapped into ETH and spread across several wallets, making it difficult to trace.
The scammer was able to make the transaction without ever hacking the system, simply exploiting the victim’s trust in the address-history feature.
Why This Matters: A Simple Mistake That Can Cost Millions
Address poisoning is an attack that relies on human error, not technology. In a world where security breaches and hacks often grab headlines, it’s easy to overlook these subtle scams that exploit user habits. The victim’s mistake was simple: they trusted the convenience of copying an address from their transaction history instead of verifying the full wallet ID.
The Takeaway: Technology Growing As Risks
The rapid innovations are made to ease the human workings and loads. But at the same time, some bad actors also take advantage of this. They use the vulnerabilities and users too much dependence on technology ease as a crime tool.
From exploiting exchanges, crypto applications, private keys, to using third party loops holes, fake websites, smart contract bugs, and deploying scams, the attackers have sharpened their tactics. They find flaws of every possible system, especially in crypto space which somehow has more gaps due to its complete on-chain nature.
This scam is a painful reminder of how easily trust can be exploited. Are you taking the necessary precautions to avoid such mistakes?
In Conclusion: Protecting Yourself
This event brings about the importance of raising awareness regarding address poisoning scams and others alike in the world of crypto.
Verify Wallet Addresses: You must always ensure that you verify the complete address while sending crypto to someone. Do not copy it from the history of any transactions.
Enable two factor authentication. Enable Two-Factor Authentication. Enable two factor authentication.
Be Aware of ‘Phishing’: Avoid clicking on malicious links or sharing your private keys.
Store Private Keys – Store them offline and secure.
Use Trusted Platforms: Trade on recognized exchanges.
If you find yourself a victim of a scam or security incident, you should report the matter to the support staff of the platform concerned, as well as the appropriate authority. Incident reporting enables the relevant authority to analyze scams and the new techniques involved by scammers, thereby enhancing security.

