North Korean Hackers Still Rake in Crypto Billions—Sanctions Be Damned
Pyongyang’s cybercriminals are laughing all the way to the (blockchain) bank.
The Lazarus loophole: Despite global sanctions tightening, North Korea’s hacker armies continue siphoning crypto through decentralized exchanges and privacy coins. Their toolkit? A mix of chain-hopping, cross-border mining ops, and good old-fashioned wallet spoofing.
Where the money flows: Trace the transactions and you’ll find a trail of laundered stablecoins funding everything from missile tests to luxury imports—because nothing says ‘rogue state’ like buying BMWs with stolen Tether.
The compliance irony: While regulators obsess over KYC for grandma’s Bitcoin purchase, state-sponsored hackers are cashing out through middlemen who’d sell their own mothers for a 2% mixer fee.
Another day, another exploit—and Wall Street still thinks CBDCs will solve everything.
Cyber alliance
The latest OFAC’s action followed a series of coordinated moves by U.S. agencies, including the Department of Justice and the FBI. On June 5, 2025, the DOJ also filed a civil forfeiture complaint seeking to seize over $7.7 million in crypto, NFTs, and other digital assets believed to be linked to the same North Korean network.
TRM Labs says the workers used identities like “Joshua Palmer” and “Alex Hong” to get hired at crypto startups and other tech firms. They were paid in stablecoins, with proceeds routed through centralized exchanges, self-hosted wallets, and then on to higher-level regime figures like Kim Sang Man and Sim Hyon Sop, both already under U.S. sanctions.
The DOJ’s investigation, according to analysts, revealed that parts of the operation relied on infrastructure based in Russia and the UAE. Investigators found the use of local IP addresses and forged documentation, which helped the North Korean workers hide their true identities. This, they said, underscored just how international the scheme had become.
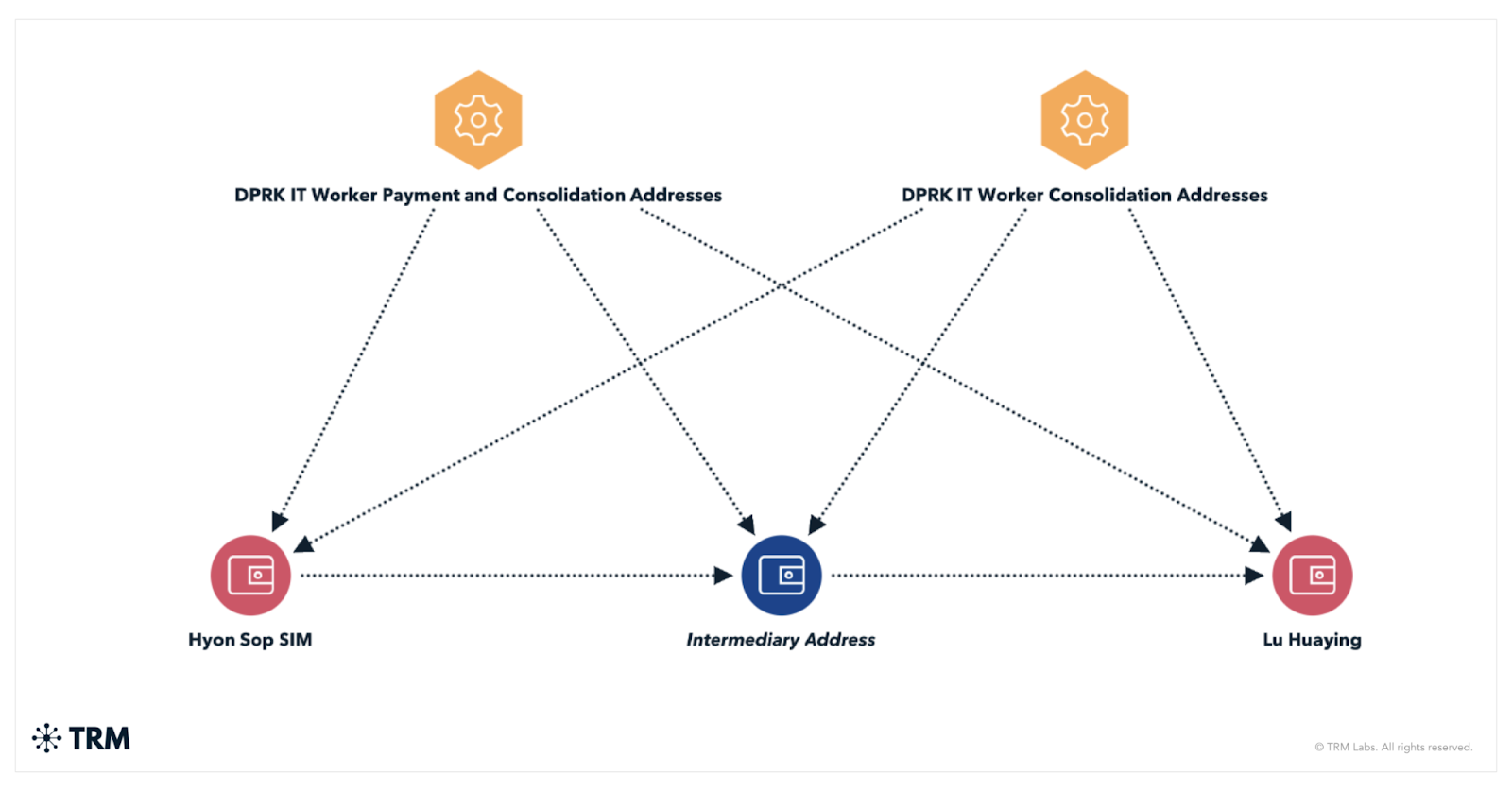
Blockchain data reviewed by TRM showed that once funds reached mid-level wallets, the money was split into smaller portions, routed through privacy-enhancing tools, and eventually exchanged for fiat via OTC desks. One of those OTC brokers had already been sanctioned by OFAC in late 2024.
As for law enforcement efforts, the FBI and other agencies successfully seized a portion of the laundered digital assets, including USDC, ETH, and some high-value NFTs. The analysts described these seizures as part of a broader laundering strategy meant to break up the money trail and make detection far more difficult.
TRM Labs says the U.S. government’s latest action sends a message that crypto remains a high-risk channel for sanctions evasion, especially when it comes to North Korean operations. The blockchain intel firm warned that companies hiring remote developers — especially in the blockchain space — need to take extra care in verifying who they’re really dealing with.

