LockBit’s Dark Web Empire Crumbles—Hackers Expose Ransomware Bitcoin Stash
In a plot twist worthy of a cyberthriller, LockBit’s ransomware operation got a taste of its own medicine. Hackers breached their dark web portal, dumping the group’s entire database—including private Bitcoin keys linked to extortion payments.
The irony? A criminal enterprise built on hacking others just got hacked harder. Security analysts are already tracing the exposed wallets—some holding funds from high-profile attacks on hospitals and infrastructure.
Meanwhile in finance circles: Traders are ironically cheering the leak as a ’proof-of-work’ for blockchain transparency—while quietly wondering if their own exchange’s security would survive a bored script-kiddie.
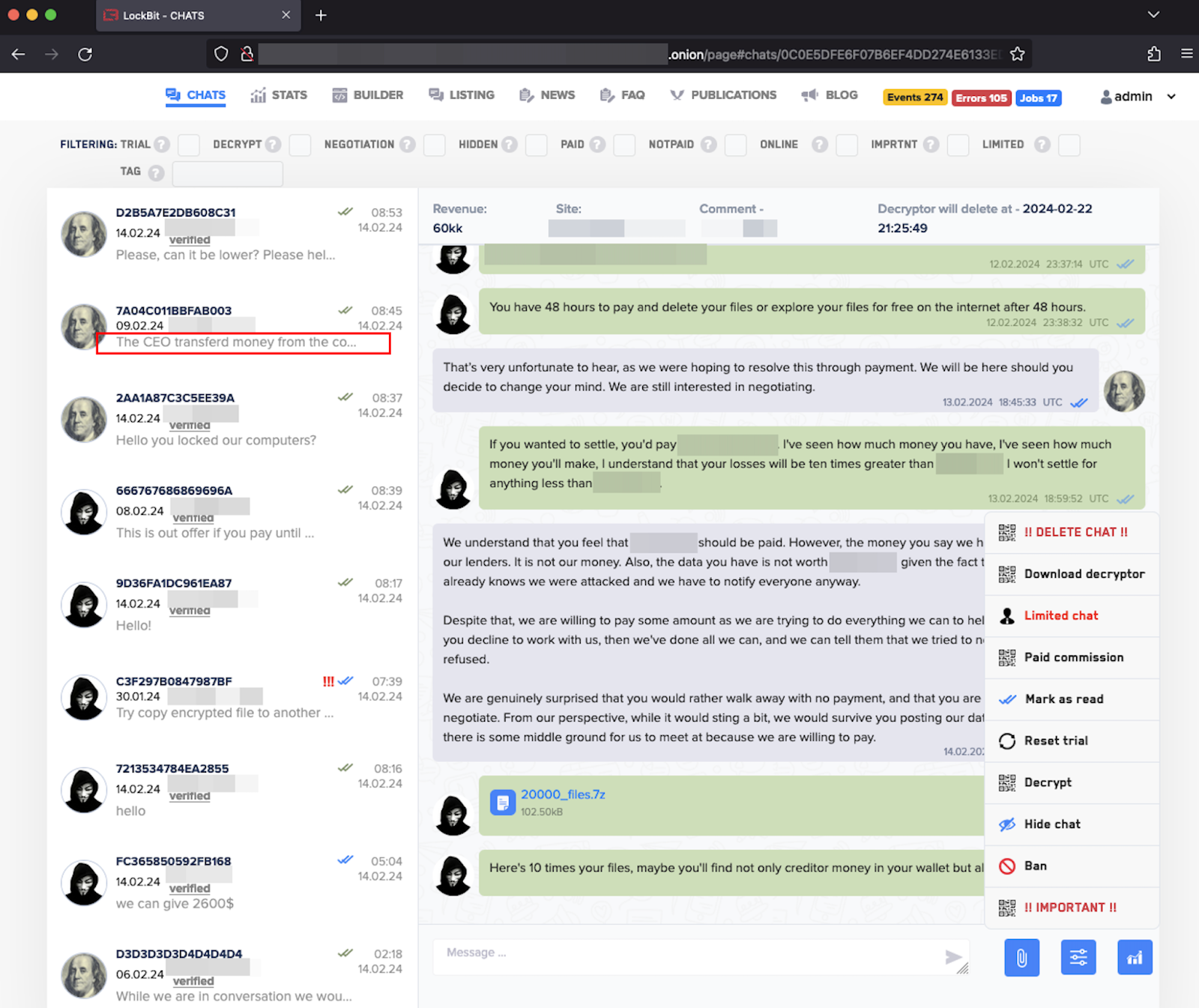 LockBit’s internal web interface | Source: SlowMist
LockBit’s internal web interface | Source: SlowMist
The attackers also appear to have gained access to a lightweight PHP-based management platform used by LockBit.
“[…] we speculate that the hacker from ‘Prague’ likely exploited a PHP 0-day or 1-day vulnerability to compromise the web backend and management console.”
SlowMist
LockBit later responded in Russian on its official channel. When asked whether the group was “pwned,” LockBit claimed that “only the lightweight panel with an authorization code was breached,” reassuring that “no decryptors were stolen, and no company data was affected.”
When asked if the hack WOULD damage its reputation, LockBit admitted that it “affects” its reputation, but reiterated that the source code “was not stolen” and that the group is “already working on recovery.” Ironically, LockBit is now offering a bounty for information on the hacker, despite the U.S. government having previously offered up to $15 million in rewards for information on LockBit members.

