German Authorities Freeze $38M in Stolen Crypto Tied to Bybit’s $1.4B Hack
German police just delivered a gut punch to crypto thieves—seizing $38 million linked to the 2024 Bybit exchange heist. The funds were traced through decentralized mixers before hitting a traditional fiat off-ramp (because even hackers need Lambos).
Forensic breadcrumbs: Chainalysis tools tracked the stolen funds across 15,000 transactions before investigators pounced. The recovered amount represents just 2.7% of the total stolen—enough to buy a small island, but barely a rounding error in crypto-crime terms.
Regulators are already spinning this as a ’win’—never mind that 97% of the loot remains missing. Meanwhile, Bybit users continue waiting for reimbursements while exchange lawyers argue about ’force majeure.’ Just another day in decentralized finance.
eXch’s Role in Crypto Laundering and its Unlawful Operations
Launched in 2014, eXch marketed itself as a privacy-centric “swapping” service, offering users the ability to exchange crypto assets across various blockchains without requiring identity verification or adhering to Anti-Money Laundering (AML) regulations.
This noncompliance made it a magnet for criminals looking to “wash” stolen funds and conceal their origins through obfuscation tactics such as token hopping, cross-chain bridges, and multiple wallets.
According to the BKA’s findings, eXch was used in laundering over €1.75 billion ($1.9 billion) worth of crypto, a large portion of which is suspected to originate from criminal activities.
Crypto security analyst ZachXBT, who has previously exposed some of the industry’s largest hacks and laundering operations, confirmed that eXch also played a major role in processing funds from other high-profile incidents.
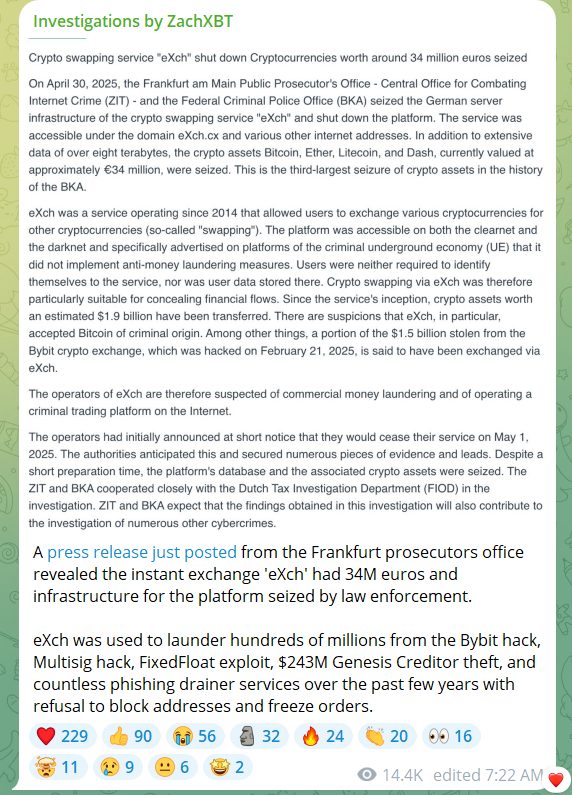
This includes the multisig wallet exploits, FixedFloat exchange-related laundering, the $243 million Genesis creditor heist, and numerous phishing drainers and rug pulls over the past few years.
ZachXBT further revealed that eXch ignored repeated warnings, refused to block malicious wallet addresses, and did not comply with freeze orders issued by regulators or intelligence-led investigators.
Additionally, according to ZachXBT’s February 22 Telegram post, even the North Korean Lazarus Group allegedly used eXch to launder over 5,000 ETH stolen from the Bybit hack.
This detail links eXch to state-sponsored cybercrime, which elevates the geopolitical importance of the investigation.
Platform Denial, Sudden Shutdown, and Official Response
In April, eXch denied helping launder stolen funds for the Lazarus Group. It said only a small portion of the Bybit hack funds passed through its system.
 eXch has denied allegations of laundering money for North Korea’s #Lazarus Group following the $1.4 billion hack on @Bybit_Official
eXch has denied allegations of laundering money for North Korea’s #Lazarus Group following the $1.4 billion hack on @Bybit_Official
on February 21.#eXch #Bybithttps://t.co/FWTnP5hiJS
Soon after, the platform announced it WOULD shut down by May 1, blaming increasing pressure and signals intelligence targeting its servers.
 Privacy-focused crypto exchange eXch will shut down on May 1 following scrutiny over alleged ties to North Korea’s Lazarus Group.#bybithack #eXchhttps://t.co/ZXQCBVbotz
Privacy-focused crypto exchange eXch will shut down on May 1 following scrutiny over alleged ties to North Korea’s Lazarus Group.#bybithack #eXchhttps://t.co/ZXQCBVbotz
However, eXch’s shutdown didn’t last. On April 27, the suspension notice disappeared, and the site resumed operations.
 Despite shutdown claims, crypto mixer eXch still launders illicit funds via active API, linked to Bybit hack and CSAM funding, warns @trmlabs.#CryptoCrime #CryptoMixerhttps://t.co/DQBOEYPnR3
Despite shutdown claims, crypto mixer eXch still launders illicit funds via active API, linked to Bybit hack and CSAM funding, warns @trmlabs.#CryptoCrime #CryptoMixerhttps://t.co/DQBOEYPnR3
A report from TRM Labs revealed that eXch never really shut down. While its websites went offline, its backend API stayed active. This allowed users to continue moving funds using eXch’s signature laundering method, which involves mixing funds in pools that hide where the money comes from.
TRM found that eXch was still being used by criminal groups, including the Lazarus Group and those linked to child sexual abuse material (CSAM).
Over $300,000 connected to CSAM has passed through eXch, with more expected. The system also made it hard to tell which funds were clean or criminal.

