Matcha Meta Breach: $16.8M Vanishes in SwapNet Exploit — Revoke Access Now
Another day, another protocol bleeding digital gold.
The SwapNet vulnerability didn't just siphon funds—it opened a firehose, draining $16.8 million from Matcha Meta's liquidity pools before anyone could hit the kill switch. The exploit bypassed standard security checks, cutting through permission layers like they weren't even there.
How the Drain Worked
Attackers found a flaw in the smart contract's logic—a tiny crack in the foundation. They used it to spoof transaction approvals, tricking the system into releasing funds that should have been locked down. No fancy zero-day needed, just a clever manipulation of existing functions. The entire heist played out in minutes, a stark reminder that in DeFi, code is law until it's not.
The Immediate Fallout
Panic spread faster than the transaction confirmations. Users flooded social channels, scrambling to check their wallets. The protocol's team issued an emergency alert, urging everyone to revoke all connected contract permissions immediately. Exchanges froze related deposits, creating a liquidity chokehold that made the situation feel even more dire.
A Pattern, Not an Anomaly
This breach fits a familiar, grim pattern. It's the third major exploit targeting cross-chain swap infrastructure this quarter. Each time, the promise of seamless interoperability crashes into the reality of complex, vulnerable code. The industry keeps building faster, but the security audits can't seem to keep pace.
What Users Must Do Now
Revoke. Every. Single. Approval. Don't just check the obvious places—scan for old, forgotten permissions tied to the affected contracts. Use a blockchain explorer or a dedicated revoke tool. Consider moving remaining funds to a fresh, cold wallet entirely. And maybe, just maybe, question why we keep handing unlimited spending authority to apps in the first place.
The silver lining? It's a brutal, multi-million dollar lesson in self-custody. In traditional finance, you get a call from the fraud department. In crypto, you get a transaction hash and a community post telling you it's already too late. The bulls keep charging, but sometimes they're running straight off a cliff.
The protocol urged affected users to immediately revoke approvals connected to SwapNet’s router contract, warning that failure to do so could leave wallets vulnerable to further unauthorized transfers.
$17M Vanishes in Seconds: How Matcha Hackers Slipped Funds Onto Ethereum
Blockchain security firms quickly began tracking the exploit as funds moved on-chain.
PeckShield reported that approximately $16.8 million had been drained in total, with the attacker swapping around $10.5 million in USDC for roughly 3,655 ETH on the Base network before starting to bridge assets to Ethereum.
#PeckShieldAlert Matcha Meta has reported a security breach involving SwapNet. Users who opted out of "One-Time Approvals" are at risk.
So far, ~$16.8M worth of crypto has been drained.
On #Base, the attacker swapped ~10.5M $USDC for ~3,655 $ETH and has begun bridging funds to… https://t.co/QOyV4IU3P3 pic.twitter.com/6OOJd9cvyF
CertiK independently flagged suspicious transactions, identifying one wallet that siphoned about $13.3 million in USDC on Base and converted the funds into wrapped Ether.
Both firms pointed to a vulnerability in the SwapNet contract that allowed arbitrary calls, enabling the attacker to transfer tokens that users had previously approved.
1/ The vulnerability seems to be in arbitrary call in @0xswapnet contract that let attacker to transfer funds approved to it. (https://t.co/B7ux5zzMLS)
The team have temporarily disabled their contracts is actively investigating.https://t.co/NBNvzxHCRw
Please revoke approval…
Matcha later clarified that the incident was not connected to 0x’s AllowanceHolder or Settler contracts, which underpin its One-Time Approval system.
The team noted that users who interacted with Matcha using One-Time Approvals were not affected, as this design limits how much access a third-party contract can retain.
After reviewing with 0x's protocol team, we have confirmed that the nature of the incident was not associated with 0x's AllowanceHolder or Settler contracts.
Users who have interacted with Matcha Meta via One-Time Approval are thus safe.
Users who have disabled One-Time… https://t.co/VQVmj4LL0F
![]()
The exposure, the team said, applied only to users who opted out of that system and granted ongoing allowances directly to aggregator contracts. In response, Matcha has removed the option for users to set such direct approvals going forward.
Old Token Approvals Emerge as a Persistent DeFi Weak Spot
The breach highlights a recurring tension in DeFi between flexibility and safety. Token approvals, while necessary for interacting with smart contracts, have long been a weak point, particularly when permissions remain active long after a transaction is completed.
In this case, previously granted allowances became the pathway for the exploit once the SwapNet contract was compromised.
The incident arrives amid continued concerns over smart-contract security across the crypto sector.
SlowMist’s year-end report shows that vulnerabilities in smart contracts accounted for just over 30% of crypto exploits in 2025, making them the leading cause of losses.
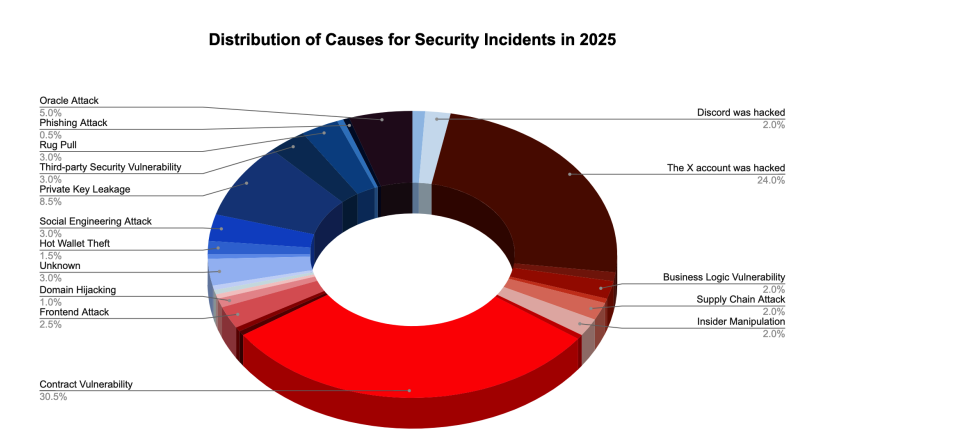
Researchers have also warned that advances in artificial intelligence are accelerating how quickly attackers can identify and exploit weaknesses in on-chain code.
While overall crypto losses declined in December, falling about 60% month-on-month to roughly $76 million, security firms cautioned that the drop did not reflect a structural improvement.
![]() Crypto-related losses from hacks and cybersecurity exploits fell sharply in December, dropping 60% month-on-month to about $76 million.#Crypto #Hackhttps://t.co/mke6K8sLVQ
Crypto-related losses from hacks and cybersecurity exploits fell sharply in December, dropping 60% month-on-month to about $76 million.#Crypto #Hackhttps://t.co/mke6K8sLVQ
PeckShield noted that a single address-poisoning scam accounted for $50 million of December’s losses, showing how concentrated and severe individual incidents can be even during quieter periods.
January has already seen several notable exploits. IPOR Labs confirmed a $336,000 attack on its USDC Fusion Optimizer vault on Arbitrum, while Truebit disclosed a smart-contract incident that on-chain analysts estimate drained more than 8,500 ETH, triggering a near-total collapse in the project’s token price.
Last week, Layer-1 network Saga paused its SagaEVM chain after an exploit moved close to $7 million in assets to Ethereum.

