North Korea’s Crypto Heists Hit $2B in 2025 Alone, Total Loot Now Tops $6.75B
North Korean hackers just had another banner year—if your definition of 'banner year' involves stealing billions from the very infrastructure meant to secure digital assets.
The Lazarus Group and other state-linked actors didn't just siphon funds; they executed surgical strikes on exchanges and protocols, exploiting smart contract vulnerabilities and social engineering with chilling efficiency. Their 2025 haul? A cool $2 billion. Their all-time total? A staggering $6.75 billion.
Where the Money's Going
Forget numbered Swiss accounts. This capital fuels Pyongyang's weapons programs and circumvents crushing international sanctions. It's a shadow economy, powered by blockchain exploits and laundered through a maze of mixers and cross-chain bridges. Tracing the funds is a digital cat-and-mouse game that often ends with the mouse vanishing into thin air.
The Security Wake-Up Call
This isn't just theft; it's a persistent stress test on crypto's core promise of security. Each breach exposes a weak link—a rushed audit, a phishing-prone employee, an over-collateralized bridge. The industry's response has been a frantic race to harden defenses, with security firms now offering 'nation-state threat' packages as a standard service. It's the ultimate proof that in high finance, whether digital or traditional, someone's always trying to rob the vault—the methods just got an upgrade.
The cynical take? Wall Street bankers get bonuses for moving decimal points; North Korean hackers get entire weapons programs funded for doing the same thing on a different ledger. The asset class is maturing—it's attracting professional, state-sponsored thieves.
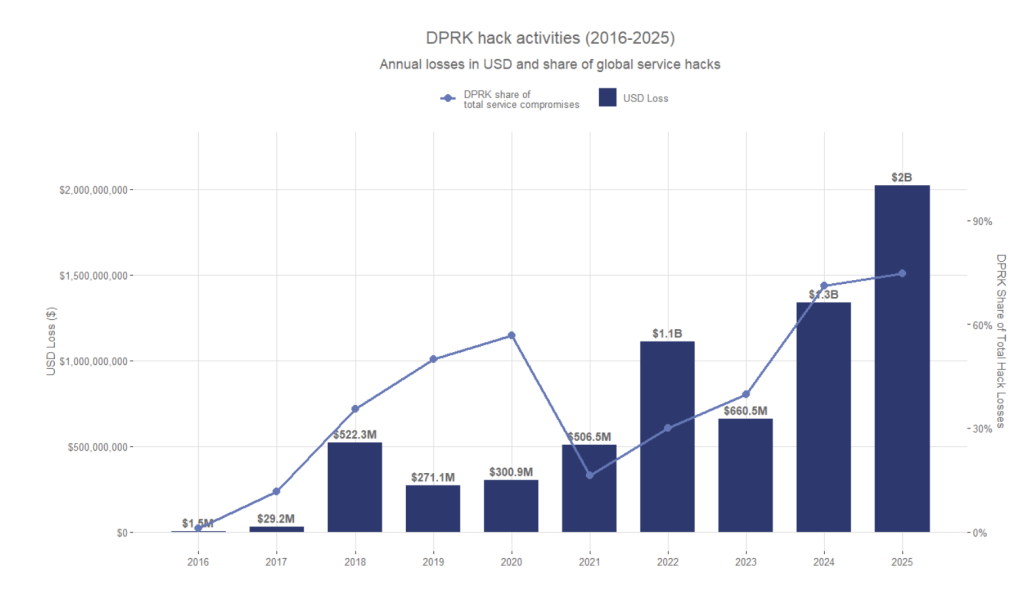
Image Source: Chainalysis
This jump came even as investigators assessed fewer confirmed incidents, a sign that a small number of hits now do more damage than a long list of smaller breaches.
Embedded IT Workers Enable High-Impact Breaches
Chainalysis said the top three hacks in 2025 made up 69% of all service losses, and the largest incident crossed 1,000 times the median theft for the first time.
One driver is access. Chainalysis said DPRK-linked actors increasingly embed IT workers inside crypto services to gain privileged access, then use that foothold to enable high-impact compromises across exchanges, custodians and Web3 firms.
The report also framed private key compromises as a recurring fault line for centralized platforms, where rare failures still dominate the loss tally when they happen.
Chainalysis said private key compromises drove 88% of losses in the first quarter of 2025, even at firms with institutional resources and professional security teams.
At the same time, the personal-wallet problem grew wider, even as the average hit got smaller.
South Korean Probe Links Solana Wallet Breach To DPRK Actors
South Korean officials and several cybersecurity firms believe the Nov. 2025 breach of Upbit’s solana hot wallet was carried out by Lazarus, North Korea’s state-backed hacking group, in an attack that siphoned roughly 44.5 billion won, or about $30 to $36 million, in Solana-based tokens.
Chainalysis estimated theft incidents surged to 158,000 in 2025 with at least 80,000 victims, and said the total stolen from individuals fell to $713 million, suggesting attackers targeted more users for less per victim.
When DPRK-linked funds move, they often MOVE with discipline. Chainalysis described a structured, multi-wave laundering pathway that typically unfolds over roughly 45 days after major hacks, starting with rapid layering, then integration through selected venues, and finishing with conversion-focused touchpoints.
It also flagged distinctive operational choices, including heavy use of Chinese-language money movement and guarantee services, plus strong reliance on bridges and mixing services, while showing less interest in lending protocols and P2P venues than other stolen-fund actors.
Even the on-chain “shape” looks different. Chainalysis said DPRK laundering concentrates slightly over 60% of volume below $500,000 per transfer, while other actors more often send funds in $1M to $10M plus tranches, a pattern it framed as a sign of sophisticated structuring.

