North Korean Hackers Infiltrate Web3 Projects as Fake IT Staff—Steal $1 Million in Crypto
Cybercriminals from North Korea are at it again—this time, posing as IT support to drain $1 million from unsuspecting Web3 projects. The Lazarus Group’s latest scheme proves even decentralized finance isn’t immune to old-school social engineering.
How They Pulled It Off
Posing as freelance developers, the hackers slipped into project Discords and Telegram groups. Once inside, they ‘offered assistance’—only to deploy malware that emptied wallets. Classic ‘help me help you’… straight into their offshore accounts.
Security Wake-Up Call
While Web3 preaches ‘trustless’ systems, human trust remains the weakest link. Projects are scrambling to implement stricter verification—but as usual, the fixes come after the breach. Meanwhile, that stolen $1 million? Probably funding someone’s missile program—because nothing says ‘financial innovation’ like laundering crypto for dictators.
Attacked Web3 projects and the losses incurred
According to on-chain analyst ZackXBT, these attackers gained insider access to projects like Favrr, Replicandy, and ChainSaw, among others, by posing as legitimate tech workers.
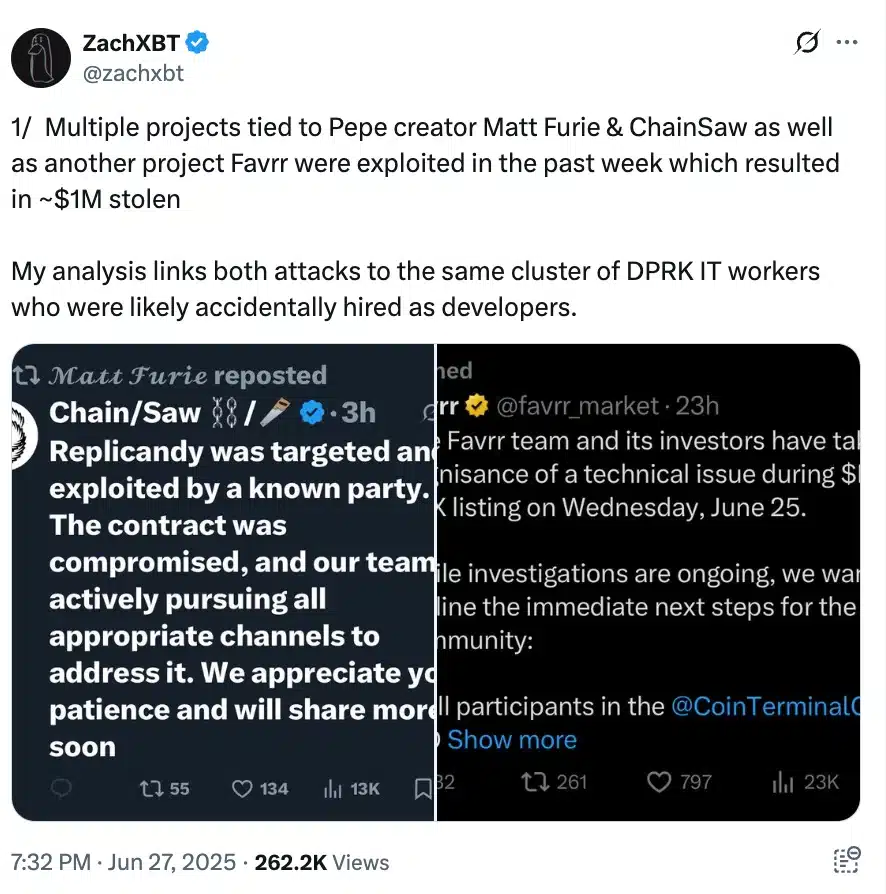
Source: ZachXBT/X
Once inside, they manipulated the NFT minting systems to generate large batches of tokens, offloaded them at scale, and triggered a collapse in market value.
The exploit not only drained funds but also destabilized the affected ecosystems, exposing serious vulnerabilities in internal access control and project security.
The timeline of the Replicandy exploit reveals a methodically executed breach, with strong indicators linking it to North Korean IT operatives.
How was the hack carried out?
On the 18th of June, ownership of the Replicandy contract was quietly transferred to a new address (0x9Fca), which later withdrew mint proceeds and resumed minting, eventually crashing the floor price by flooding the market with NFTs.
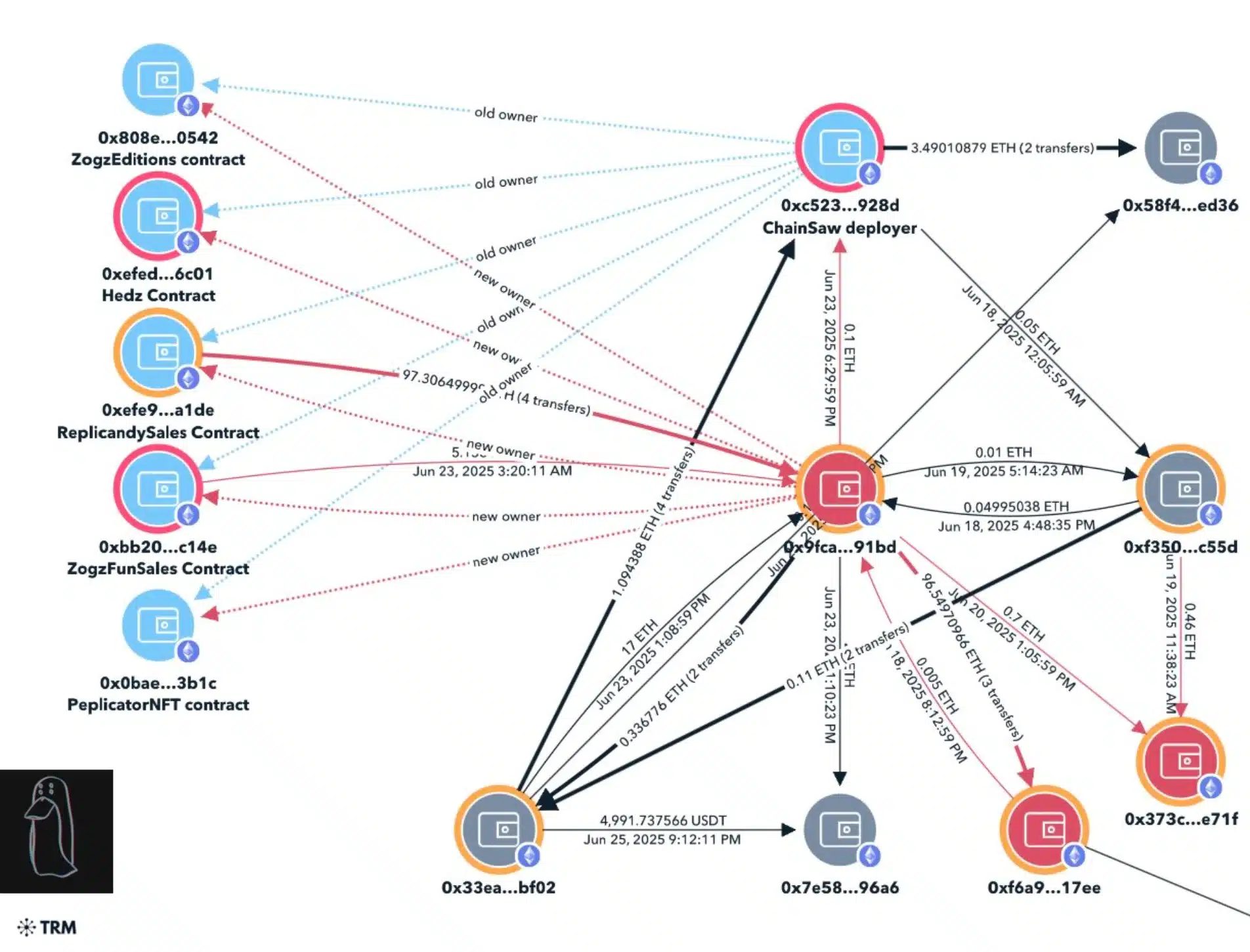
Source: ZachXBT/X
This pattern was once again repeated on the 23rd of June with additional collections, Peplicator, Hedz, and Zogz, causing further devaluation and losses totaling over $310,000.
On-chain analysis traced the stolen funds through multiple wallets, ultimately uncovering USDT deposits funneled to MEXC and identifying two suspicious GitHub developer accounts — ‘devmad119’ and ‘sujitb2114’, linked to the breach.
Internal logs further exposed inconsistencies, such as developers claiming to be U.S.-based while using Korean language settings, Asia/Russia time zones, and Astral VPNs.
These red flags strongly suggest the attackers were part of a coordinated North Korean campaign exploiting lax vetting procedures in Web3 hiring.
While the Favrr team responded swiftly with enhanced user safety measures, Chainsaw only issued a brief warning and later deleted it.
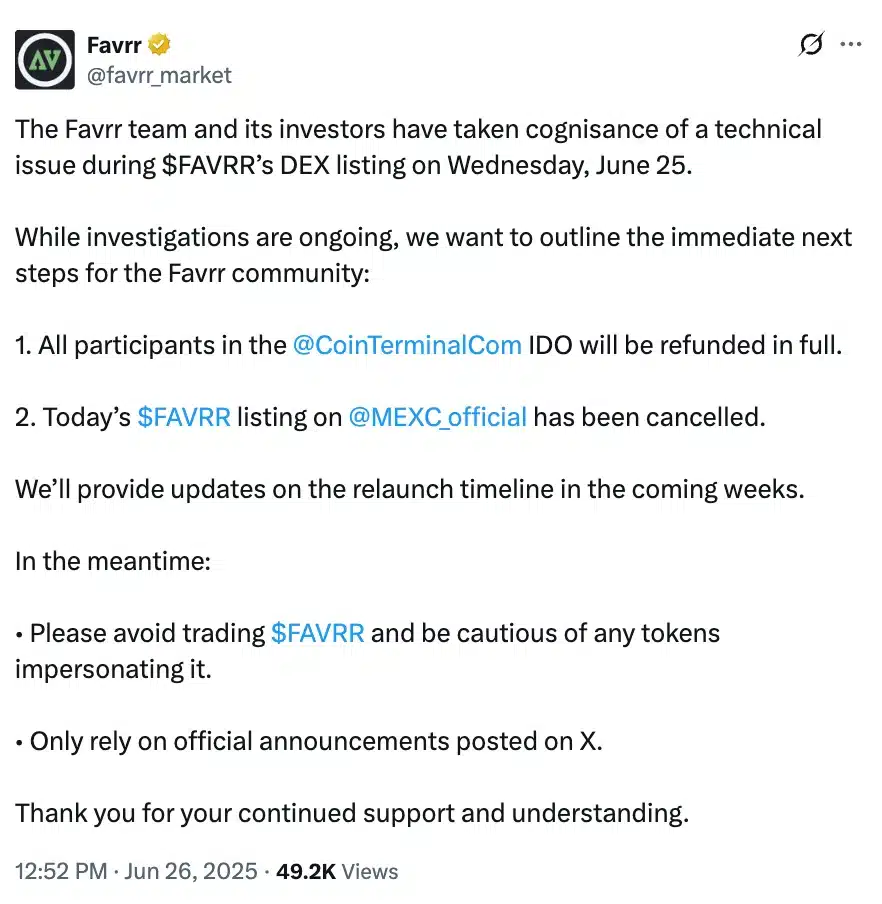
Source: Favrr/X
On the other hand, Matt Furie has remained completely silent, hinting that the broader picture points to a far more troubling reality.
The rise of North Korean hackers
That being said, North Korean-linked hackers have become increasingly aggressive in 2025, with researchers attributing over $1.6 billion, roughly 70% of all stolen crypto this year, to state-affiliated groups.
The staggering $1.5 billion Bybit breach in February, now believed to be their work, stands as the largest crypto theft in history.
These actors, including the notorious Ruby Sleet group, have extended their reach beyond crypto, previously infiltrating U.S. defense contractors and now targeting IT firms through fake hiring campaigns and elaborate social engineering tactics.
In response to the growing wave of crypto-related fraud and security breaches, nations across the globe are stepping up regulatory safeguards.
In the United States, the TRUMP administration is actively advancing a series of pro-crypto policies designed to shield the industry from discriminatory banking practices and excessive regulatory pressure.
These include a pending executive order to prohibit financial institutions from targeting crypto firms, efforts to roll back SEC-imposed restrictions like SAB 121, and legislative support for frameworks such as the GENIUS Act to clarify rules for stablecoins and digital assets.
Meanwhile, Australia has moved swiftly to address crypto ATM misuse by capping cash transactions at AU$5,000, enforcing stricter identity checks, and requiring real-time scam warnings.
Together, these measures reflect a coordinated international shift toward a more secure and accountable Web3 environment.
Subscribe to our must read daily newsletter

