Mass NPM Attack Rocks Crypto: Is Ledger Still SAFU in 2025?
Another day, another supply chain attack—but this one hits different. The JavaScript ecosystem just got rocked by a massive NPM campaign targeting crypto wallets and DeFi apps. Over 1,300 malicious packages flooded the registry, mimicking legitimate libraries to hijack developer workflows.
Ledger's security showdown
Hardware wallet giant Ledger finds itself in the crosshairs. Attackers cloned their Connect Kit dependency, pushing poisoned updates to unsuspecting projects. The playbook? Old-school typosquatting meets modern crypto-thievery.
Crypto's dependency dilemma
Open-source infrastructure remains both crypto's greatest strength and its most glaring vulnerability. The attack exposes the fragile trust model underlying billion-dollar protocols. One compromised package can drain fortunes faster than a hedge fund manager spotting a tax loophole.
SAFU or sorry?
Ledger's response team swung into action, but the incident raises uncomfortable questions. How many projects installed the malicious packages? Were any funds actually compromised? The community watches—wallets half-open, half-closed—waiting for the all-clear signal that might not come.
This isn't just about stolen coins. It's about trust erosion in the tools that power the entire digital asset space. Because nothing says 'decentralized future' like a centralized package registry bringing everything to its knees.
![]() There’s a large-scale supply chain attack in progress: the NPM account of a reputable developer has been compromised. The affected packages have already been downloaded over 1 billion times, meaning the entire JavaScript ecosystem may be at risk.
There’s a large-scale supply chain attack in progress: the NPM account of a reputable developer has been compromised. The affected packages have already been downloaded over 1 billion times, meaning the entire JavaScript ecosystem may be at risk.
The malicious payload works…
— Charles Guillemet (@P3b7_) September 8, 2025
How Did The NPM Attack Happen?
Josh Junon, who also goes by ‘qix’ in the developer world, is the package maintainer whose accounts were hijacked in this supply-chain attack. Junon confirmed the incident yesterday (September 8), taking to the Blue Sky social media platform to state that he was aware of the compromise and adding that the phishing email came from a spoof NPM support account.
In the emails, the attackers threatened that the targeted maintainers’ accounts WOULD be locked on September 10th, 2025, as a scare tactic to get them to click on the link redirecting them to the phishing sites.
“As part of our ongoing commitment to account security, we request that all users update their Two-Factor Authentication (2FA) credentials. Our records indicate that it has been over 12 months since your last 2FA update,” the phishing email reads.
“To maintain the security and integrity of your account, we kindly ask that you complete this update at your earliest convenience. Please note that accounts with outdated 2FA credentials will be temporarily locked starting September 10, 2025, to prevent unauthorized access.”
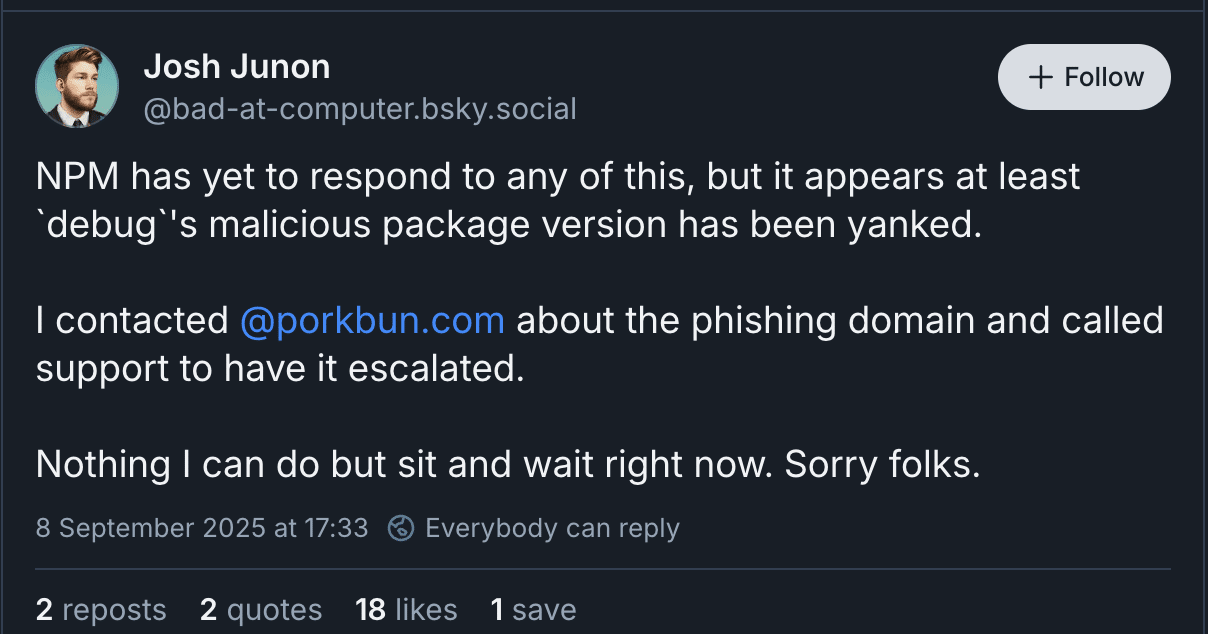
(SOURCE)
According to reports from those who received the phishing message, the attackers used the same email to target other package maintainers and developers.
Since the incident was detected, the NPM team has removed some of the malicious versions published by the attackers, including the one for the debug package, which is downloaded 357.6 million times per week.
The malicious code only impacts individuals accessing the compromised applications over the web, monitoring for cryptocurrency addresses and transactions that are then redirected to attacker-controlled wallet addresses. This causes the transaction to be hijacked by the attackers rather than being sent to the intended address.
The malware operates by injecting itself into the web browser, monitoring wallet addresses and transactions across the biggest blockchains such as Ethereum, Bitcoin, Solana, Tron, and Avalanche. On network responses with crypto transactions, it replaces the destinations with attacker-controlled addresses and hijacks transactions before they’re signed.
Hardware Wallet Firm Ledger Responds to The NPM Attack: “Ledger Devices Are Not And Have Not Been At Risk”
With warnings from security experts on social media to crypto traders, hardware wallet firm Ledger quickly addressed the NPM attack situation, boldly stating that Ledger devices are not at risk.
The official Ledger account on X made the following statement;
“Ledger devices are not and have not been at risk during an ecosystem-wide software supply chain attack that was discovered. Ledger devices are built specifically to protect users against attacks like these.
Only Ledger devices have secure screens, powered by the Secure Element chip, to ensure what you see on-screen is exactly what you sign. Ledger devices support Clear Signing, enabling human-readable transaction details for verification, and Transaction Check on-device, which warns users of potential scams.
Remember: never blind sign, and always verify addresses before you approve transactions. Your private keys and recovery phrase remain safe. Clear signing on the secure screen means you always see the real address before approving.”
Right now, the most at-risk wallets are ‘hot wallets’, which are self-custodial Web3 wallets such as MetaMask, Rabby, Phantom, etc. While hardware wallets allow a user to see the destination address before signing a transaction, hot wallets offer no such option, making them more vulnerable to attacks.
Hacker Has Hilariously Managed To Steal Just $159 Since Exploiting NPM
There has been a total of $159 stolen so far in the NPM supply chain attack.
These coins were sent to addresses tagged in the original write-up shared by Ledger’s CTO. https://t.co/wDWHrxwNIP pic.twitter.com/hQOQLdepO1
— Arkham (@arkham) September 8, 2025
While the hacker has caused widespread fear throughout the crypto market, Arkham Intelligence data shows that the individual responsible has only managed to drain $159 from users so far.
That figure has since increased to over $500, but it appears to be from traders sending the hacker meme coins, rather than proceeds from the hack. The hacker’s wallet now holds various amounts of BRETT, GONDOLA, VISTA, DORKY, amongst others.
Although the hacker sending meme coins has added a LAYER of brevity to the situation, traders should still exercise caution when interacting with any on-chain wallet, as there has been no communication from NPM to confirm that the attack has been entirely contained.
Keep an eye on the official @npmjs account for confirmation that the vulnerabilities have been contained and crypto traders’ funds are SAFU.

